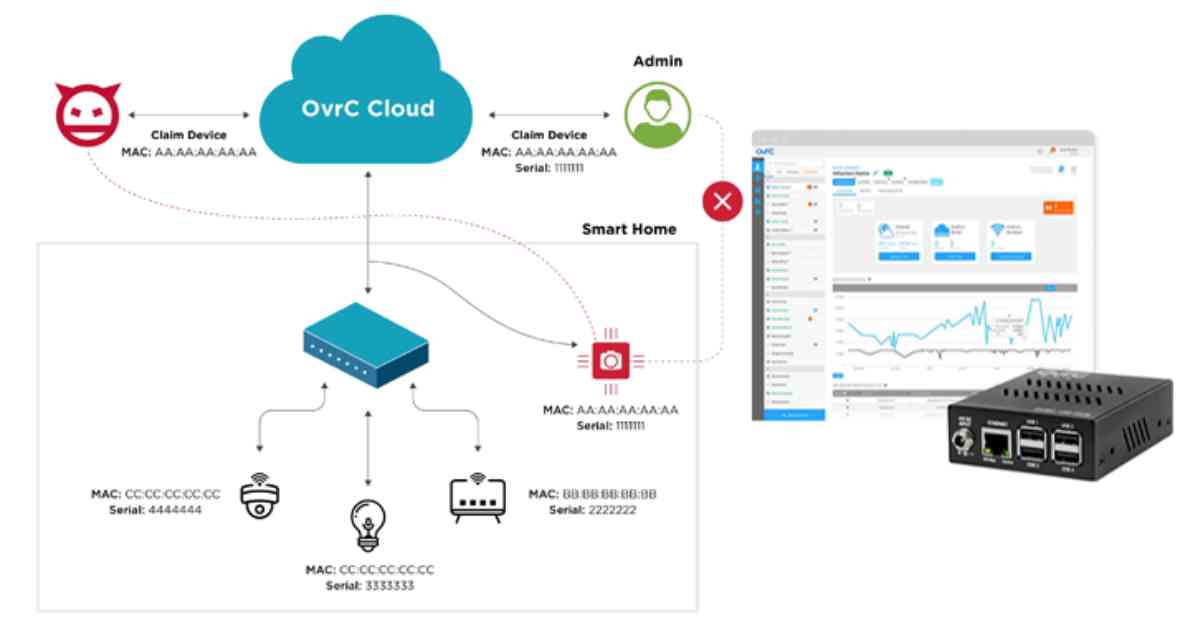
A recent security analysis of the OvrC cloud platform has revealed 10 vulnerabilities that could potentially be exploited by attackers to remotely execute code on connected devices. This could allow attackers to access and disrupt various devices such as smart power supplies, cameras, routers, home automation systems, and more.
The OvrC platform, developed by Snap One, is designed to provide remote management, configuration, and troubleshooting of IoT devices on networks. However, researchers have identified flaws that could be chained together to allow attackers to impersonate devices, execute arbitrary code, and disclose sensitive information.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an advisory highlighting the risks associated with these vulnerabilities. Snap One has released fixes for eight of the vulnerabilities in May 2023, with the remaining two addressed on November 12, 2024.
The vulnerabilities stem from issues related to the device-to-cloud interface, including weak identifiers, access controls, authentication bypasses, input validation failures, hardcoded credentials, and remote code execution flaws. These flaws could potentially allow attackers to bypass firewalls, gain unauthorized access to cloud-based management interfaces, enumerate devices, hijack devices, elevate privileges, and run arbitrary code.
Some of the most severe vulnerabilities identified include CVE-2023-28649, CVE-2023-31241, CVE-2023-28386, and CVE-2024-50381, which have the potential to allow attackers to impersonate hubs, claim unclaimed devices, upload arbitrary firmware updates, and unclaim devices arbitrarily.
It is crucial for manufacturers and cloud service providers to prioritize the security of IoT devices and connections, especially as the number of connected devices continues to grow. Failure to address these security issues could have significant consequences for devices connected to the OvrC cloud, including power supplies, routers, home automation systems, and more.
In addition to the vulnerabilities in the OvrC platform, security flaws have also been discovered in EmbedThis GoAhead, a web server used in embedded and IoT devices. These vulnerabilities have been patched in the latest version of GoAhead to prevent potential denial-of-service attacks.
Furthermore, security shortcomings have been identified in Johnson Controls’ exacqVision Web Service, which could be exploited to take control of video streams from surveillance cameras and steal credentials.
As the number of IoT devices continues to increase, it is essential for companies to prioritize security and regularly update their systems to protect against potential cyber threats. Stay informed about the latest security updates and follow us on Twitter and LinkedIn for more exclusive content.