Tag: Cybersecurity
Decade of Cyber Defense Excellence: NJCCIC Success Story
Alright, so on May 21, 2025, the New Jersey Office of Homeland Security and Preparedness (NJOHSP) was all about celebrating the 10-year anniversary of...
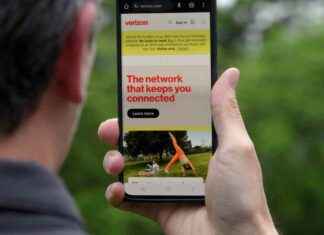
Creepy Cell Phone Scam: Insta Posts About Wife & Unordered DoorDash
They were in an Uber heading to the airport for a family trip to Florida when the call came in. It was Verizon. The...
Risks and Benefits of Free Wi-Fi: How to Stay Safe
Public Wi-Fi is a ubiquitous feature in our lives today, offering convenience at every turn. But as we revel in its accessibility, we must...
Why Elon Musk’s DOGE Poses National Security Concerns
The recent surge in young tech specialists hired by Elon Musk to streamline U.S. government processes has sparked concerns among national security experts. These...
Breakthrough Proof System Collaboration Between Anaxi Labs and Carnegie Mellon University’s CyLab
Breakthrough Proof System Collaboration Between Anaxi Labs and Carnegie Mellon University’s CyLab Pittsburgh, United States, December 6th, 2024, Chainwire Anaxi Labs, in collaboration with Carnegie Mellon...
Securing Hybrid Cloud: Cloud Security Trends for 2025 & Beyond | Darktrace Blog
Darktrace Detects Mamba 2FA Phishing Campaign In a groundbreaking discovery, the Darktrace Threat Research team has identified a new and highly sophisticated phishing threat known...
Corporate VPN Clients: Revealed Flaws and Solutions
Corporate VPN Clients: Vulnerabilities Uncovered and Solutions Revealed Palo Alto Networks Vulnerability Researchers have recently unearthed critical vulnerabilities in the update mechanisms of two major corporate...
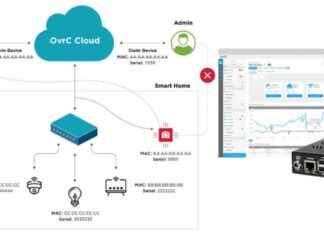
OvrC Platform Vulnerabilities: IoT Devices at Risk of Remote Attacks and Code Execution
A recent security analysis of the OvrC cloud platform has revealed 10 vulnerabilities that could potentially be exploited by attackers to remotely execute code...
AI: A Force Multiplier for Cyber Criminals | How Artificial Intelligence is Impacting Cybersecurity
Cyber security professionals in the UK are expressing growing concerns about the impact of artificial intelligence (AI) on the industry. According to the Chartered...
Collaboration between ProofID and Midships for Global Delivery of Ping Identity Services
ProofID and Midships have joined forces to offer top-notch Ping Identity Services worldwide. This collaboration, which combines two Ping Identity partners, will provide comprehensive...
Unveiling the Threat of Anxiety in Battling AI Deepfake Hackers: A $10 Billion Startup’s...
Artificial Intelligence-generated deepfake attacks are becoming more common in the realm of hacking. The technology behind these sophisticated phishing campaigns has advanced to the...
Analyzing Post Exploitation Activities on Fortinet Devices: Insights from Darktrace Blog
The recent findings from Darktrace's Threat Research team shed light on active exploitation campaigns targeting Fortinet appliances. Specifically, the analysis delves into the September...
Fortinet Edge Devices Facing Repeated Cyber Attacks
Fortinet Edge Devices Face Cyber Attacks Recently, there have been reports of hackers potentially bypassing a patch for Fortinet gateway devices, prompting a warning from...
API Edge Security: Importance and Best Practices for Protection
API Edge Security: The Key to Protecting Modern Applications As the use of APIs continues to increase across various industries, cybersecurity experts are recognizing the...
4 Key Takeaways for Software Security Teams from CISA SBOM-a-rama
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has been advocating for software bills of materials (SBOMs) as a crucial tool to enhance software...
Revolutionizing Blockchain Security: Karak and Space-Time Collaboration
Karak has recently announced a strategic partnership with Space and Time, aiming to enhance blockchain security mechanisms. This collaboration involves integrating Space and Time's...
Britney Spears’ Mansion Listed in Fake Listings After Cyber Attack
A fake sale listing for Britney Spears' mansion in Thousand Oaks, California was the result of a computer hack on the real estate site...
AI-powered application onboarding for enhanced identity security Enhanced Identity Security with AI Application Onboarding
SailPoint Technologies Inc., a company specializing in identity security, has recently introduced a new AI-powered application onboarding feature to enhance identity security for its...
Is blocking Russian media the best strategy?
Is Blocking Russian Media the Best Strategy? Western Governments Crack Down on Russian News Outlets Amid National Security Concerns In the wake of Russia's invasion of...
Tech brain drain fuels Philippines’ cybersecurity skills gap
Tech Brain Drain Worsens Cybersecurity Skills Gap in the Philippines Commuters queue at a bus station in Mandaluyong, Philippines, July 15, 2022. (Reuters/Lisa Marie David) The...